If you have researched “how Cloudflare DDoS protection works” on Google, you probably have come across comments like, “The free version of Cloudflare can be easily bypassed for purposes like DDoS attacks and cannot protect my website adequately from attacks. In fact, this is a false point of view because this is caused by the user who was not able to correctly configure the server or Cloudflare.

How to Prevent DDoS Attacks
First of all, when configuring your Cloudflare settings you should make sure that your IP address is being hidden. If you configure your server’s firewall which only visitors coming from Cloudflare proxy are allowed, then you can protect yourself from attacks that directly target the IP address of your site.
Of course, you should first know about managing a server, you should analyze the logs for any unusual situation, and you should also know how big the attack is before making any decisions.
The free version of Cloudflare provides you with unlimited protection, regardless of the size of DDoS attacks, including Layer 7 DDoS attacks – Of course, the paid versions offer extra options according to your needs, however, it doesn’t mean that you have to pay for a higher level of protection when you are under a really huge attack.
If you are sure that you have configured the essential settings, regarding the server and Cloudflare, during the attack you can simply activate the “I’m Under Attack” mode via the Cloudflare Dashboard. In this way, you can prevent many attacks.
A Large DDoS Attack
A few days ago, I saw a topic about DDoS on a forum site. A website hosted in shared hosting was having trouble collapsing with incoming DDoS attacks, although it is being secured by Cloudflare. These attacks were continuing after transferring it to VDS and the new server was collapsing again.
Of course, finding the source of the problem in Cloudflare would be the easy and wrong way. I offered them to transfer their server to Vultr, which is a powerful and secure cloud server provider, and I was going to set up the configuration of the server.
After a while, we started the transferring process. After transferring our customer’s site to the new server, the attacks continued. The site was under a huge attack.
The attackers were trying to stop the server from answering by making billions of query requests with random letters such as /?s=abc , /?s=xyz .
In the last 24 hours, more than 291,000,000 requests have been sent to the server.
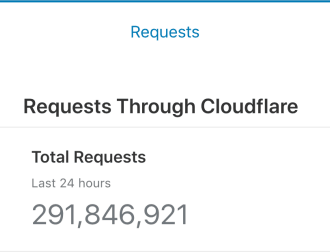
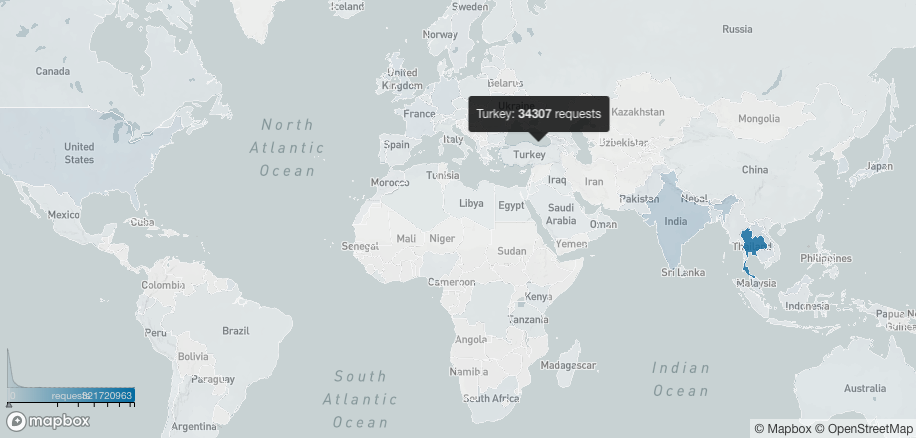
We took a look and saw that 34,307 HTTP requests were made from Turkey over one week. If we consider the fact that that site is Turkish and only used by Turkish users, the requests of the real visitors are a small part in comparison to the requests made by the attackers.
DDoS attacks can affect the limits of the server’s bandwidth. In this attack, more than 1.21TB in less than 24 hours can be seen.
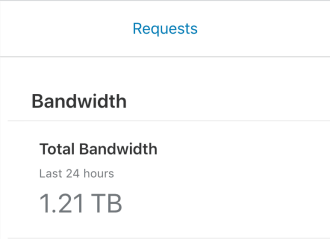
Luckily, this dataflow was between the attackers and Cloudflare. The server wasn’t affected by it.
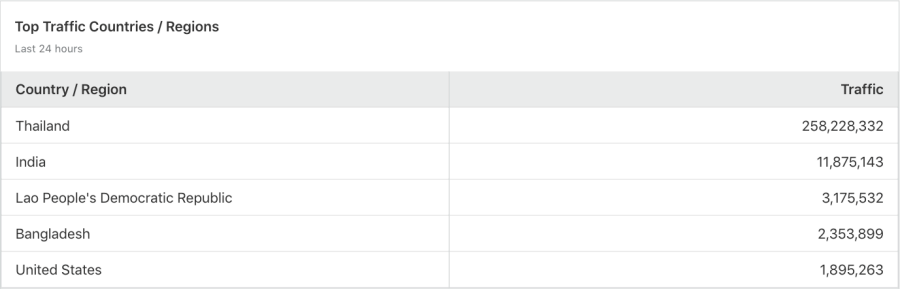
The attackers kept on attacking for more than 48 hours. They were from all around the world, mostly from Asia.
In our service, we migrate your site to the cloud servers and set up Cloudflare DDoS protection for your site. We take every precaution against the attackers, who are trying to bypass Cloudflare and reach your server. All these services are completed by us. We also offer technical help in case of an attack, so don’t waste your time!
If you think that kind of attack is possible on your site, take precautions before it is too late. If you do not take precautions, your site might not only get shot down for a long time, it may also be punished by Google.
If you have any questions or if you need consulting feel free to ask.
Cloudflare, with its unique features, will contribute to the security of your website. I recommend you choose it for all your projects. Not to mention the numerous features that Cloudflare offers to improve the speed performance of your site. 🙂
